Login Form
| Barracuda Monitoring |

|

|
| Written by Paul Winkeler | |
| Thursday, 26 February 2009 | |
|
Barracuda Neworks makes a fine line of inbound (and outbound?!) SPAM filters deployed in-line with your email server and the outside world. These devices provide a web interface both for management and configuration as well as for end-users to trawl through suspect quarantined e-mail searching for treasure. You can see how the device is performing under its current load right from the front page of this built-in website and then it can also send scheduled e-mail messages with various statistical reports. Unfortunately, what it does not do, is alert you of odd behavior in any meaningful pro-active way. After all, who has time to read through all those daily statistics reports from all their devices?! The obvious answer to this problem then is to monitor the device through our facorite Open Source monitoring platform, Zenoss but that is where we run into a glitch. It turns out that Barracudas cannot be probed with SNMP, the standard way such devices are probed until you get to the 400-series and even then, the exposed MIB is not an enterprise specific one with Barracuda goodies but just the generic OS one, courtesy of the underlying Linux engine. Ah, you say, but doesn't Barracuda make a REST-based API available? Well yes, they do, but now we're writing a command based datasource and even then, this feature is not available until the 400-series and up. Read on to learn how PBnJ Solutions built a Zenoss ZenPack to monitor Barracudas from the 200-series on up, now allowing everyone to not only get an alarm when the inbound queue is overflowing but also collect some great SPAM statistics over time. Being as that yours truly is more familiar with Perl than Python, he chose the former to implement the datasource command to retrieve statistics from Barracudas even if the latter is the Langua Franca of Zenoss. A little birdie told him that all models of Barracuda respond with an XML dump of current statistics when probed with: https://barracuda/cgi-bin/stats.cgiso in a nut-shell, the Perl script does just that using a call to wget with some miscellaneous options to suppress validation of SSL sertificates and to copy the results to stdout. For example, here is an image of the kind of history graphs this ZenPack will let you create: 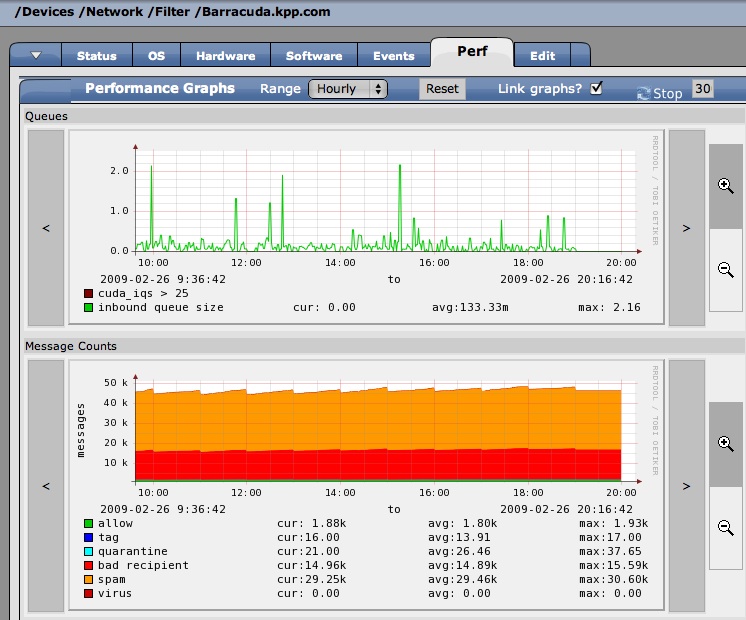
|
|
| Last Updated ( Sunday, 01 March 2009 ) |